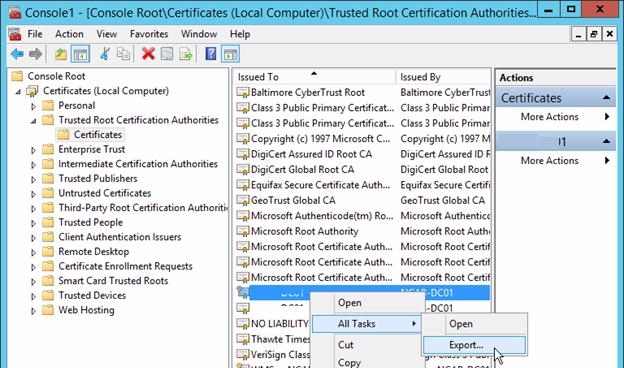
Let’s look on how to centrally deploy an SSL certificate on domain computers and add it to the Trusted Root Certification Authorities using Group Policy. After the certificate is deployed,…
Active Directory: Core Concepts, Architecture and Best Practices
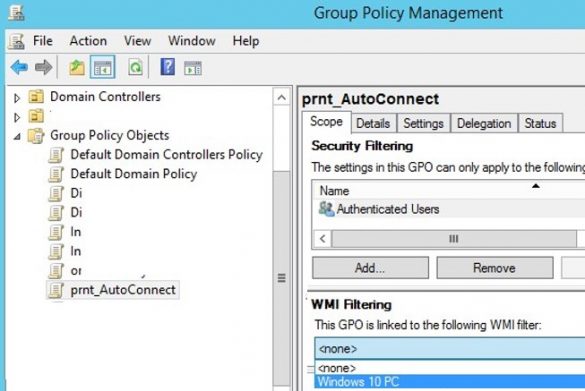
Restricting Group Policy with WMI Filtering
WMI filters in Group Policy (GPO) allow you to more flexibly apply policies to clients by using different rules. A WMI filter is a set of WMI queries (the WMI…
Let’s look at how to create a simple administrator notification system when someone adds a new user to the important Active Directory security group. For example you want to track…
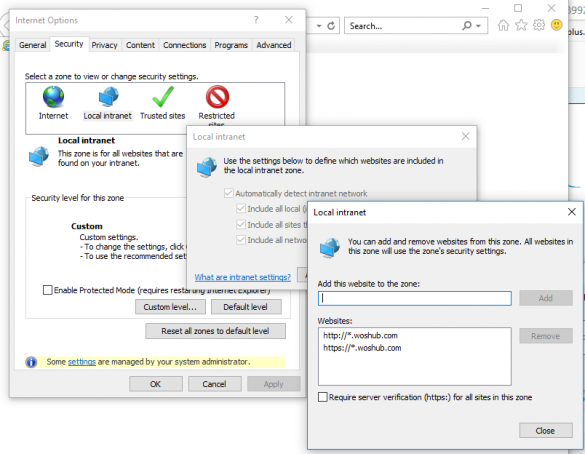
Configuring Kerberos Authentication in Different Browsers
In this article, we’ll look at how to configure Kerberos authentication for different browsers in a Windows domain to enable transparent and secure authentication on web servers without the need…
How to Check Who Reset the Password of a User in Active Directory
Let’s see how to track who reset the password of the particular user account in Active Directory using domain controllers security logs.
Today we’ll deal with the configuration peculiarities of Java SE centralized security settings on corporate computers using Windows group policies (GPO). These policies should prevent downloading and running untrusted Java…