The Server Message Block (SMB) 1.0 file-sharing protocol is disabled by default in the latest versions of Windows 11 and 10 and in Windows Server 2019/2022. This version of the protocol is insecure (vulnerable) and is not recommended for use in a network environment. Windows supports more secure versions of the SMB protocol (2.x and 3.x).
SMB v1 may only be necessary if you still have legacy Windows XP/2003 devices, old versions of NAS, SMB-enabled network printers, devices running older versions of Samba, etc. on your network. This article looks at how to enable or disable the SMB 1.0 file-sharing protocol on Windows.
Please note that the SMB protocol consists of two components that can be enabled or disabled separately:
- Client SMB 1.0 – used to access shared folders on other computers;
- Server SMB 1.0 – is enabled if your computer is used as a file server for other computers and devices.
How to Enable or Disable SMB 1.0 on Windows 10 and 11
Starting with Windows 10 1709, SMB 1.0 is disabled by default on all desktop versions of Windows but can be manually enabled.
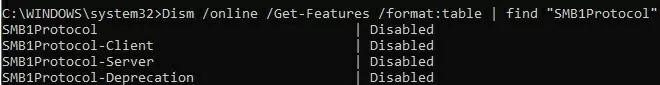
Open a command prompt and check the status of the SMBv1 protocol components in Windows using the DISM command:
Dism /online /Get-Features /format:table | find "SMB1Protocol"
In this example, you can see that all SMBv1 features are disabled:
SMB1Protocol | Disabled SMB1Protocol-Client | Disabled SMB1Protocol-Server | Disabled SMB1Protocol-Deprecation | Disabled
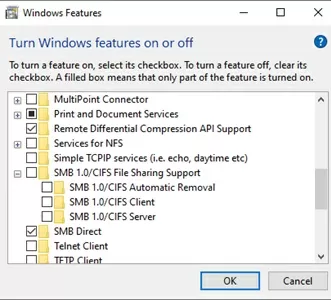
In Windows 10 and 11, you can also manage SMB 1 features from the Control Panel (optionalfeatures.exe). Expand the SMB 1.0 /CIFS File Sharing Support option. There are three 3 SMB v 1.0 features available:
- SMB 1.0/CIFS Automatic Removal
- SMB 1.0/CIFS Client
- SMB 1.0/CIFS Server
SMB Client v1.0 must be installed if your computer needs to access shared folders hosted on legacy devices. If legacy network devices need to access network folders on your computer or use its shared network printers, you need to enable the SMB 1.0 server.
You can enable SMB 1.0 client or server in Windows 10/11 from the Windows Features dialog or by using the commands:
Dism /online /Enable-Feature /FeatureName:"SMB1Protocol"
Dism /online /Enable-Feature /FeatureName:"SMB1Protocol-Client"
Dism /online /Enable-Feature /FeatureName:"SMB1Protocol-Server"
Enable-WindowsOptionalFeature -Online -FeatureName SMB1Protocol-Server
Enable-WindowsOptionalFeature -Online -FeatureName SMB1Protocol-Client
Once the SMBv1 client is enabled, it is automatically removed if it is not used for more than 15 days.
Run the following DISM commands to disable SMB 1.0 in Windows:
Dism /online /Disable-Feature /FeatureName:"SMB1Protocol"
Dism /online /Disable-Feature /FeatureName:"SMB1Protocol-Client"
Dism /online /Disable-Feature /FeatureName:"SMB1Protocol-Server"
Or use PowerShell to remove the SMB1Protocol components:
Disable-WindowsOptionalFeature -Online -FeatureName SMB1Protocol -Remove
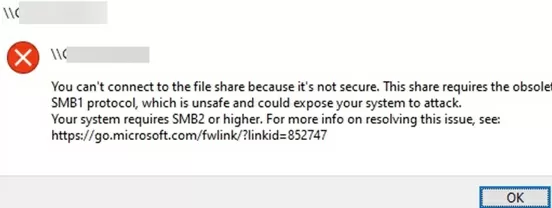
If you have disabled the SMBv1 client in Windows 10/11, you may receive the following errors when accessing a shared folder on a file server that only supports SMBv1:
0x80070035 The network path was not found;
Unable to connect to file shares because it is not secure. This share requires the obsolete SMB1 protocol, which is not secure and could expose your system to attacks;
You can’t connect to the file share because it’s not secure. This share requires the obsolete SMB1 protocol, which is unsafe and could expose your system to attack. Your system requires SMB2 or higher.
This is explained in more detail in the article “Unable to access shared folders on Windows“.
The Computer Browser service will also stop working on your computer if you disable the SMBv1 client (it is used by the legacy NetBIOS protocol to discover devices on the network).To view neighboring computers on the Windows network, you need to configure the Function Discovery Provider Host service (check this article).
Enable or Disable SMB 1.0 Protocol on Windows Server 2019/2022
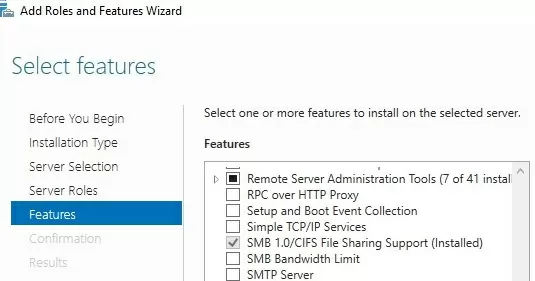
The SMBv1 protocol components are also disabled by default in Windows Server 2019 and 2022. You can install SMB v1 using the Server Manager (SMB 1.0/CIFS File Sharing Support feature) or PowerShell.
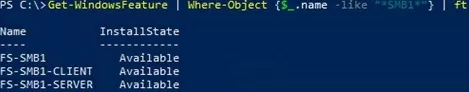
Use the PowerShell command to check whether SMB 1.0 is enabled on Windows Server:
Get-WindowsFeature | Where-Object {$_.name -eq "*SMB1*"} | ft Name,Installstate
To install the SMB 1.0 client, use the command:
Install-WindowsFeature FS-SMB1-CLIENT
Enable SMB 1.0 server:
Install-WindowsFeature FS-SMB1-SERVER
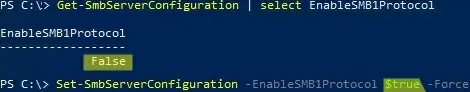
Check that the SMB1 protocol is enabled in file server settings. Enable the protocol if disabled:
Get-SmbServerConfiguration | select EnableSMB1Protocol
Set-SmbServerConfiguration -EnableSMB1Protocol $true -Force
EnableSMB1Protocol: True, then this server supports shared folder access from SMB 1.0 clients.To disable SMBv1 (requires a reboot):
Set-SmbServerConfiguration -EnableSMB1Protocol $false -Force
Disable-WindowsOptionalFeature -Online -FeatureName SMB1Protocol
To completely remove SMB1 components from the Windows image:
Uninstall-WindowsFeature -Name FS-SMB1 -Remove
sc.exe config lanmanworkstation depend= bowser/mrxsmb20/nsi
sc.exe config mrxsmb10 start= disabledAudit SMB 1.0 Access on Windows File Servers
Before disabling and completely removing the SMB 1.0 driver on the file server side, it is a good idea to make sure that there are no legacy clients on the network that use the SMB v1.0 protocol to connect to shared folders. To find such clients, you must enable auditing of access to the file server via the SMB1 protocol:
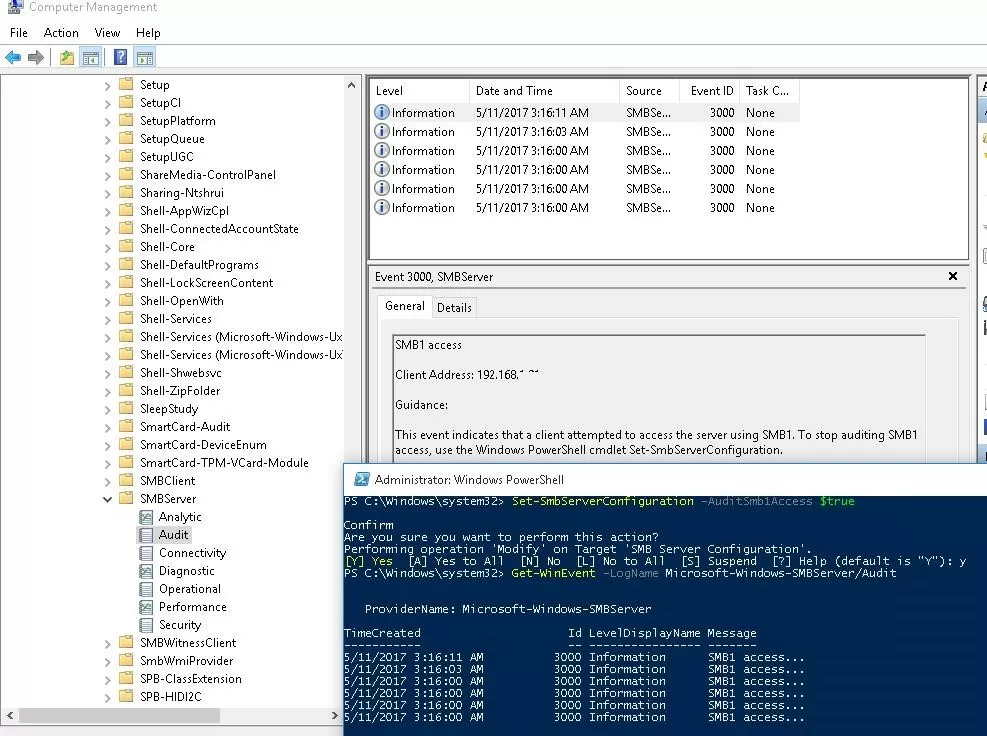
Set-SmbServerConfiguration –AuditSmb1Access $true
After several days, open the Event Viewer on the server, check the log Applications and Services -> Microsoft -> Windows -> SMBServer -> Audit, and check for any attempts to access the file server via the SMB1 protocol.
Get-WinEvent -LogName Microsoft-Windows-SMBServer/AuditCheck the Event Viewer logs and look for the entry with the EventID 3000 from the SMBServer source, which indicates that client 192.168.1.10 is trying to access the server using the SMB1 protocol.
SMB1 access Client Address: 192.168.1.10 Guidance: This event indicates that a client attempted to access the server using SMB1. To stop auditing SMB1 access, use the Windows PowerShell cmdlet Set-SmbServerConfiguration.
Find a computer or device on your network with this IP address. If possible, update the operating system or firmware to a version that supports the more secure SMBv2 or SMBv3 protocols. If you are unable to update such a client, you will need to enable SMBv1 on your file server.
To find all computers in Active Directory with SMB v1 enabled, run the command:
Get-ADComputer -Filter {(enabled -eq $True) } | % {Invoke-Command -ComputerName $_.DNSHostName -scriptblock {If ( (Get-ItemProperty -path "HKLM:\SYSTEM\CurrentControlSet\Services\LanmanServer\Parameters").SMB1 -eq 1 ) {Write-Output "SMBv1 is enabled on ${env:computername}"}}}
This command uses the Get-ADComputer cmdlet to get the list of enabled computers in the domain. It then uses Invoke-Command to connect to each computer via PowerShell Remoting and checks if SMB 1.0 is enabled.
Disable SMB 1.0 via Group Policy
If there are no legacy devices on your network that only support SMB 1.0, you must completely disable this protocol version on all computers. You can implement a GPO that forces the SMB 1.0 protocol to be disabled to prevent users from manually installing and enabling SMB 1.0 features on their computers. As there is no separate SMB configuration policy in the standard Windows Group Policy templates, you will need to disable it using the registry policy.
- Open the Group Policy Management console (
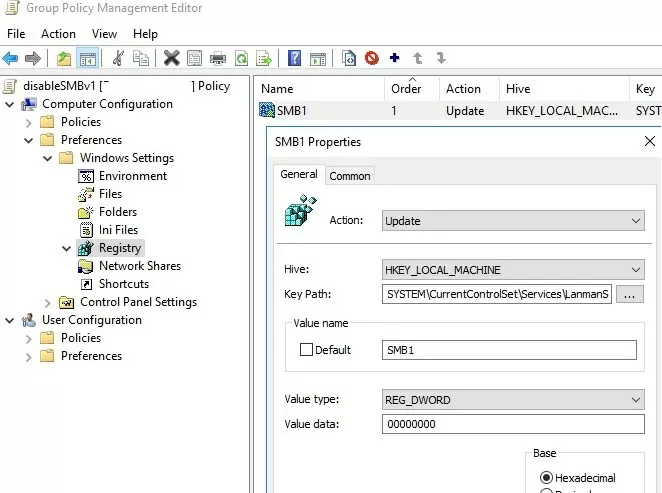
gpmc.msc), create a new GPO (disableSMBv1), and link it to the OU containing the computers where you want to disable SMB 1.0; - Edit the policy and navigate to Computer Configuration -> Preferences -> Windows Settings -> Registry;
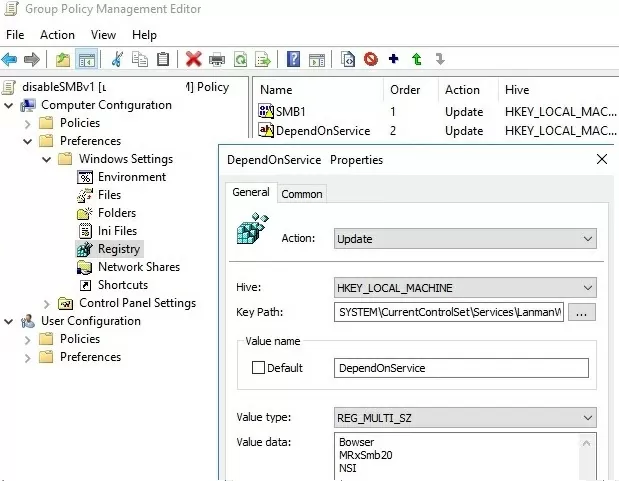
- Create a new Registry Item with the following setting:
Action:Update
Hive:HKEY_LOCAL_MACHINE
Key Path:SYSTEM\CurrentControlSet\Services\LanmanServer\Parameters
Value name:SMB1
Value type:REG_DWORD
Value data:0
- This policy will disable the SMBv1 server component.You can exclude certain versions of Windows from this policy by using the WMI GPO filter.
If you want to use the GPO to disable the SMB client on domain computers, create two additional registry parameters:
- The Start parameter (REG_DWORD type) with value 4 in the registry key HKLM\SYSTEM\CurrentControlSet\services\mrxsmb10;
- The DependOnService parameter (REG_MULTI_SZ type) with the value Bowser, MRxSmb20, NSI (each value on a new line) in the reg key HKLM\SYSTEM\CurrentControlSet\Services\LanmanWorkstation.
All you need to do is update the Group Policy settings on the clients and then, after the reboot, check that SMBv1 is completely disabled.
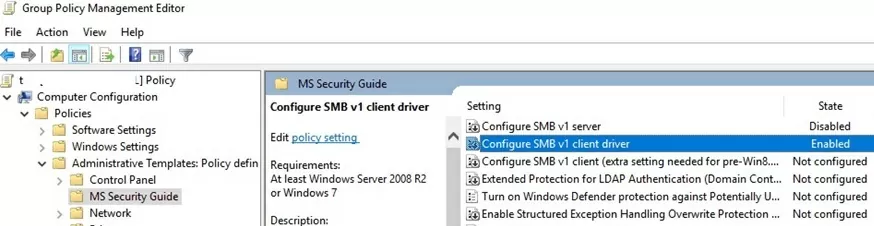
SecGuide.adml and SecGuide.admx files):- Configure SMB v1 server;
- Configure SMB v1 client driver.
5 comments
cool thank you
Excelente articulo
I have found out that i have a chicken / egg situation. If i disable SMB1 on the domain workstations these wont be able to contact the servers anymore and if i disable the smb1 on the servers they can’t connect to the servers either. If i use the GPO solution and i do disable the servers during the Night, will the client computers still be able to update the group policy from sysvol folder to update their policy and disable the smb1 as well ?
This way i can tell the users to reboot their computers after the first error messages appear …. Otherwise i need to figure out how to do a big bang but this will be very difficult to achieve
What about creating a small script to accomplish the task, and push out a GPO to create a scheduled task for all targeted systems to kick off simultaneously at a later, synchronized date?
Hello. I’d like to warn people about using the “Uninstall-WindowsFeature –Name FS-SMB1 –Remove” command. Unfortunately, I can’t install SMB 1.0 anymore after using this command. Now Windows complains that it can’t find the “sources” anymore.
So beware to anybody, don’t us this command hastly!